Let’s talk about 3D printing scams.
Fabbaloo friend Joel Telling put out a very interesting video last week focusing on the emerging trend of 3D print scams.
This is not the first scam in 3D print history. There have been multiple in the past, mainly in the Kickstarter area. Countless 3D printer crowdfunding campaigns have failed miserably, and some are still in progress. Most of those fails have been due to project mismanagement, but a very few seem to have been deliberately evil. In addition, there have been fake reseller sites that accept payment but never deliver anything. We wrote about one of those back in 2019, where someone “bought” a Toybox 3D printer and was defrauded.
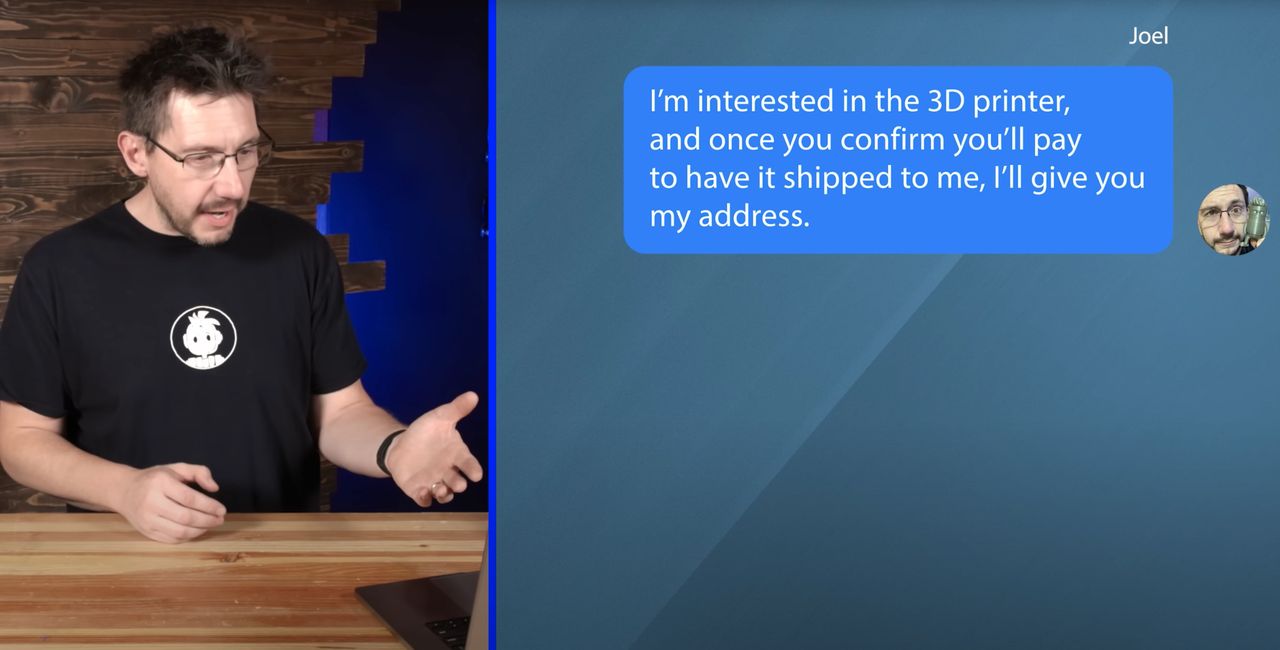
In the video, Telling received curious requests to review 3D printing equipment, which he frequently does on his popular YouTube channel, “3D Printing Nerd”.
Instead of ignoring the suspicious requests, Telling decided — in the interests of investigation — to follow up on them as if they were real.
Of course, he discovered they were indeed scams. The scam concept was to entice the product reviewer into paying for shipping for a product, but then they’d ghost away, never to be heard from again.
Telling used some innovative tricks to track down the source of the scam, which turned out to be a building in Bangladesh.
I encourage you to view the whole video, as it shows that our industry is not immune to scammers.
But there’s a bit more to this. It turns out “production scamming” is a burgeoning industry in South Asia, particularly in India, but also in Bangladesh. The general approach is to set up a kind of clandestine call center, where staffers are paid good money — relative to the area — to persuade Westerners to give them cash one way or another.
This is done through a written script they execute. The plan is to convince the respondent they must pay money for some compelling reason. Often this approach works, and sometimes unknowing folks are bilked of thousands of dollars. Usually the presentation is slightly “off”, which immediately deters anyone paying attention. This leaves the staffers with respondents that are less aware of what’s really going on.
In my research I’ve seen these call centers use quite a number of different scripts. They each have a different approach. One might require a small fee to gain a refund from Amazon. Another might be a tech support call requiring the PC owner to pay for additional virus software. You get the idea: they invent some reason for the respondent to pay that makes sense to them.
That’s what I was thinking when I watched Telling’s video: this is yet another script they’ve cooked up and deployed at their (potentially large) call center. These scripts are executed until they don’t work, and then they are replaced by new variations.
It’s criminal, obviously, and difficult to shut down. These operations prey on people outside their country of origin, so local authorities are less inclined to get involved. When they are occasionally busted, they simply set up another call center somewhere else and repeat.
These operations are a kind of “production scamming”, where large-scale techniques are used to steal money, and there doesn’t seem to be much that can be done.
Well, there’s one thing: educate people to know how to recognize them. Tips include:
- Messed up communications (text, images, process, etc.)
- Payment demanded in unusual forms (cryptocurrency, gift cards, etc.)
- Questionable email addresses
- Representing companies they clearly don’t work for
Scams emerge in any domain, so it’s not surprising it’s appeared in the 3D print space.
If you’re interested in learning more about how these production scamming operations work behind the scenes, I strongly recommend checking out Jim Browning’s Tech Support Scams YouTube channel, where Browning often directly hacks into these call centers, even live viewing from their own web cams.
Via YouTube
