An interesting research paper provides three ideas on how to detect flaws in 3D prints.
Their objective was to develop means of detecting secretly altered 3D prints, but in truth their methods could also work to detect bugs in printing operations.
The problem they’re addressing is the coming big issue of compromised 3D prints, in which a critical production piece is somehow printed incorrectly, resulting in perhaps fatal flaws in the part. Such flaws could lead to catastrophic failure of a mechanism, such as a vehicle or large machine that could cause damage to people or property.
How does a 3D print get compromised? There are two methods. One is the obvious approach, where the source STL files are secretly modified to include flaws. This cheesy video shows how that could be done by stealing the STL files and changing them.
Although it’s a bit mystifying to me how they can download an STL file, a surface shape representation of an object, and then immediately modify its CAD representation in Solidworks without downloading the Solidworks file, the point is made. Steal a file, and change it.
The other method is to jigger the firmware of the 3D printer itself to detect certain geometries and introduce flaws. For example, infill could be automatically limited to less than required levels.
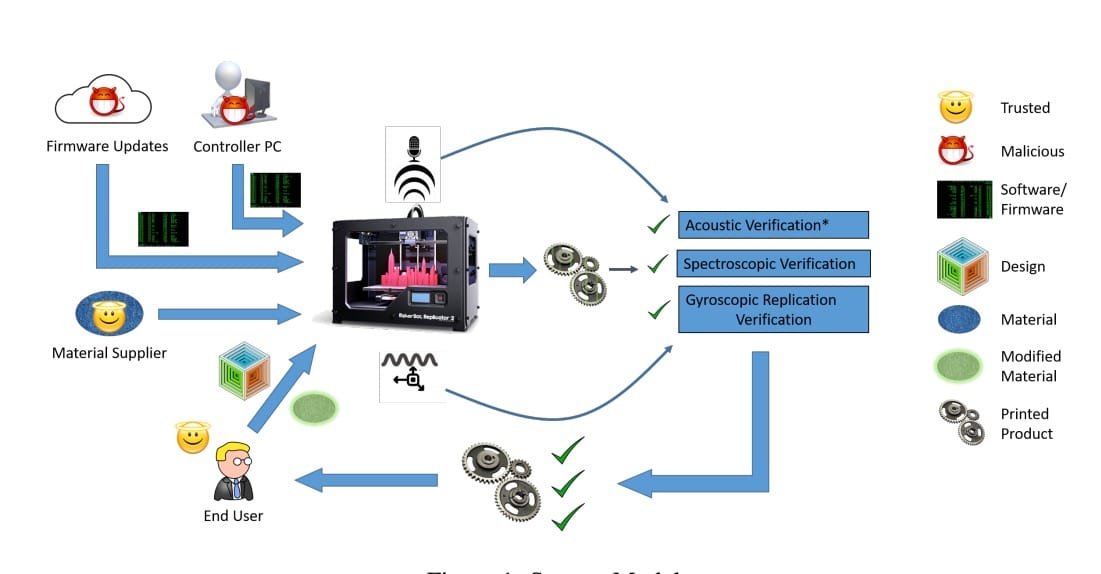
The researchers propose three approaches for validating that a correct 3D model was actually produced:
Acoustic modeling: in this approach, they literally listen to the stepper motor movements as the print proceeds, and then attempt to match them to the expected movement sounds from a correct 3D model source file. I’m not sure how accurate this could be, as 3D models and their sliced versions are quite different. Consider that you could slice a 3D model in different ways, resulting in very different audio patterns. You’d have to compare the sliced files, not the 3D model.
Spatial Tracking: Here the researchers would, with a camera system, monitor the movements of the 3D printer itself. From these movements they could theoretically match patterns with the expected GCODE movements. Again, you must compare the sliced GCODE instead of the 3D model for accuracy.
Embedded Material: This approach involves changing the material to include a small amount of detectable material. They use a particular type of nanoparticle that would otherwise be insignificant in the quality of the print, but one that is detectable by a Raman spectroscope. If the pattern of material doesn’t match what is expected, then a flaw has been found.
Note that these approaches would not prevent such corruption from happening; they merely detect that it has. And based on their nature, it’s actually possible to detect a flaw WHILE the print is taking place, and potentially be able to stop the print before it wastes everyone’s time and materials.
These methods are external to the 3D printer itself and thus have a layer of insulation between them and the compromised device. However, if future machines include these features, then they could be compromised themselves, negating this work.
At this point there is little interest in such methods, simply because the majority of 3D prints are for prototyping, not for production. But you can bet that when large numbers of production parts for critical processes and machines are being made, the interest will rise significantly.
Then we’ll see this type of approach being implemented widely.