Another year, another hacker conference, another method for 3D printing keys to previously unhackable locks.
That’s right, it’s an ongoing trend in the hacker community to demonstrate methods for bypassing security measures, both in the virtual world of software and the physical world of high-security locks.
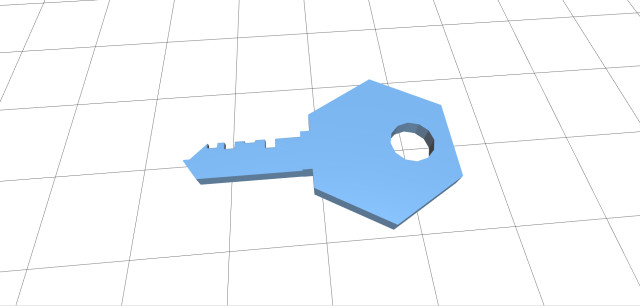
This year, at the eleventh Hackers On Planet Earth (HOPE) conference in New York City, security researchers going by the names Nite 0wl, Johnny Xmas and DarkSim905 demonstrated the ability to copy a master key for Safe Skies luggage locks, used by the Transportation Security Administration (TSA) to quickly unlock luggage during clearance checks. The 3D-printable key copy was then made public, allowing anyone to 3D print the Safe Skies master key themselves.
The TSA Master Keys
While luggage locks may prevent theft during travel, this protection is only a slight hurdle in the way of quick and easy security checks on the part of TSA agents. For this reason, the agency turned to two companies, Travel Sentry and Safe Skies, to create master keys for luggage locks. With these two manufacturers producing the majority of TSA-approved locks on the market, it would be possible both for travelers to protect their belongings and for the TSA to conduct its inspections for the sake of travel safety.
As a means of demonstrating the problematic nature of giving a third party access to your security protocols—whether it be a luggage lock or an iPhone passcode—the three hackers created their own master key for bypassing locks made by Safe Skies. To do so, Nite 0wl and Johnny Xmas purchased a wide variety of Safe Skies locks and found the common pattern that would open multiple locks.
In an interview with CSO Online, Nite Owl explained, “The big breakthrough was when I acquired several Safe Skies locks that used wafer-tumbler mechanisms instead of pin-tumbler mechanisms, because of the different mechanical design I was able to work out the master key cuts very quickly and then confirm that the key worked on all of the sample locks I had.”
To break Pandora’s box open further, the hackers converted the master key design to a 3D-printable model and uploaded the design to GitHub. Though the master key is now publicly accessible, Johnny Xmas pointed out that the same manual process employed by the hackers could be pulled off by any lockpicker.
“This was done by legally procuring actual locks, comparing the inner workings and finding the common denominator. It’s a great metaphor for how weak encryption mechanisms are broken—gather enough data, find the pattern, then just ‘math’ out a universal key (or set of keys). What we’re doing here is literally cracking physical encryption, and I fear that metaphor isn’t going to be properly delivered to the public,” he said.
Read more at ENGINEERING.com